Ping pong
Ping Pong challenge : CTFROOM INTERVARSITY COMPETITION
I got to learn a lot of new tools from this recent forensics challange I did. As part of my note-taking, I have documentated the challenge which was part of CTFROOM Intervarsity Competition .
The challenge has already been done in a walkthrough video by the creator of the challenge and is basically what I used to solve and learn the better part of the challenge.
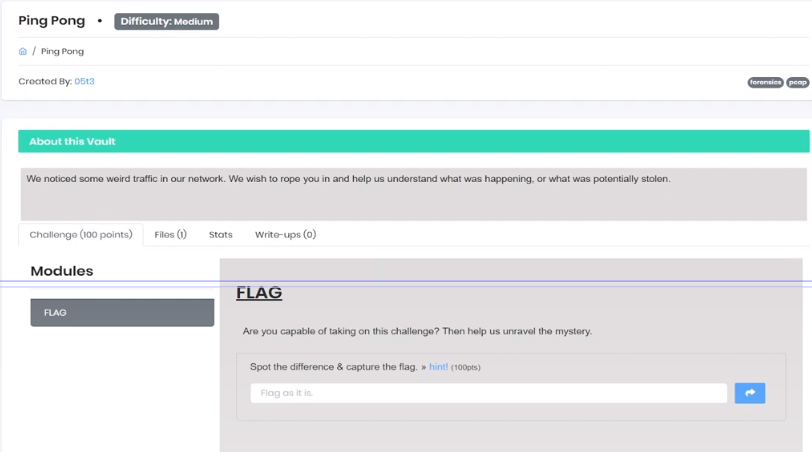
This was the landing page of the challenge with its descrpition, hints and one file.
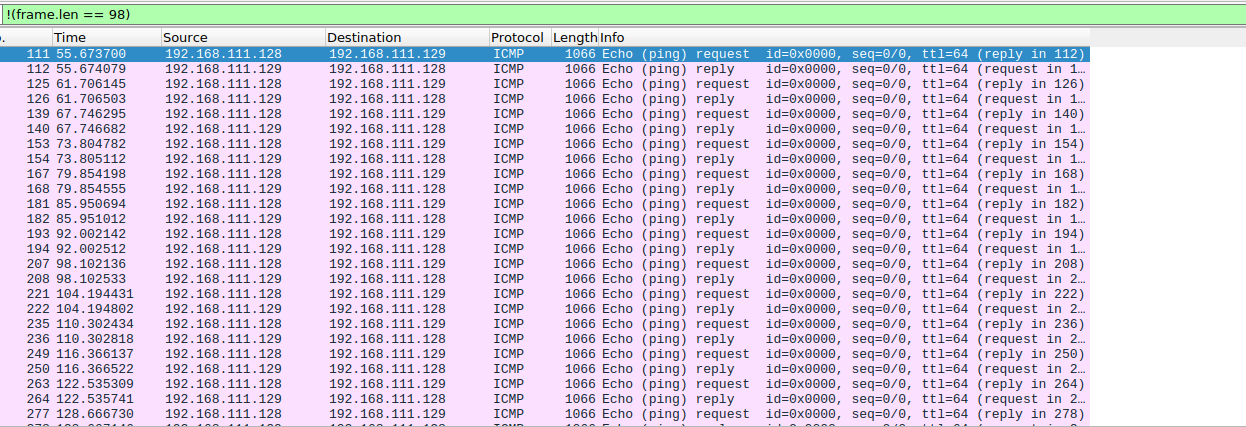
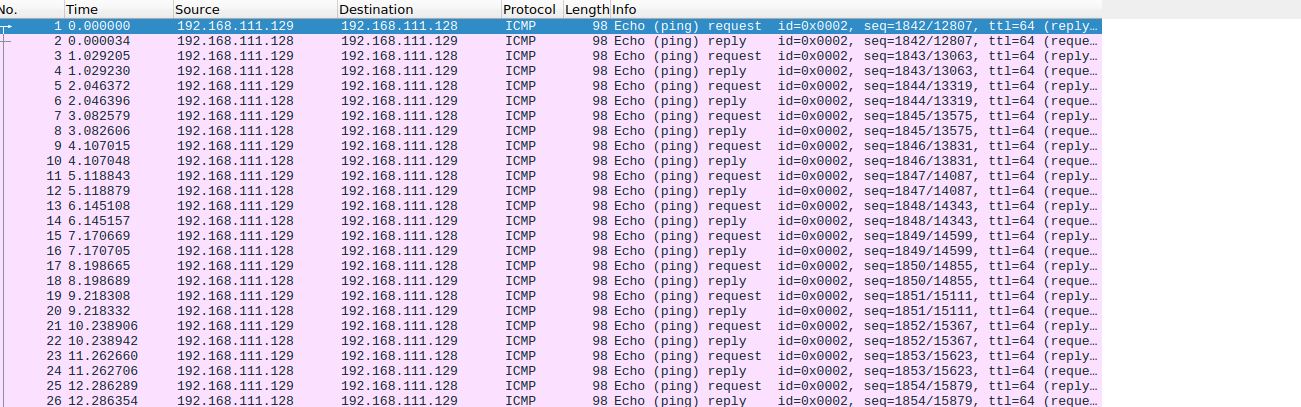
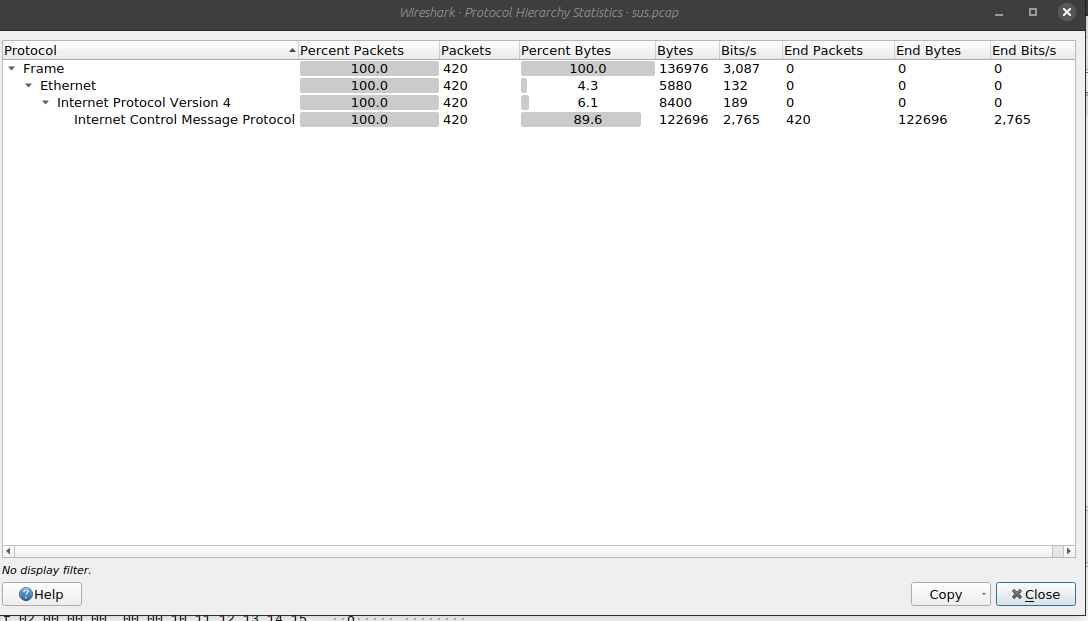
I downloaded the file and it was a pcap file. I then opened the file using wireshark and got number of captured packets.
I then used the statistics tab to get more info about the packets . The packets consisted only of one protcol which is ICMP(Internet Control Message Protocol) and a total of 420 captured packets
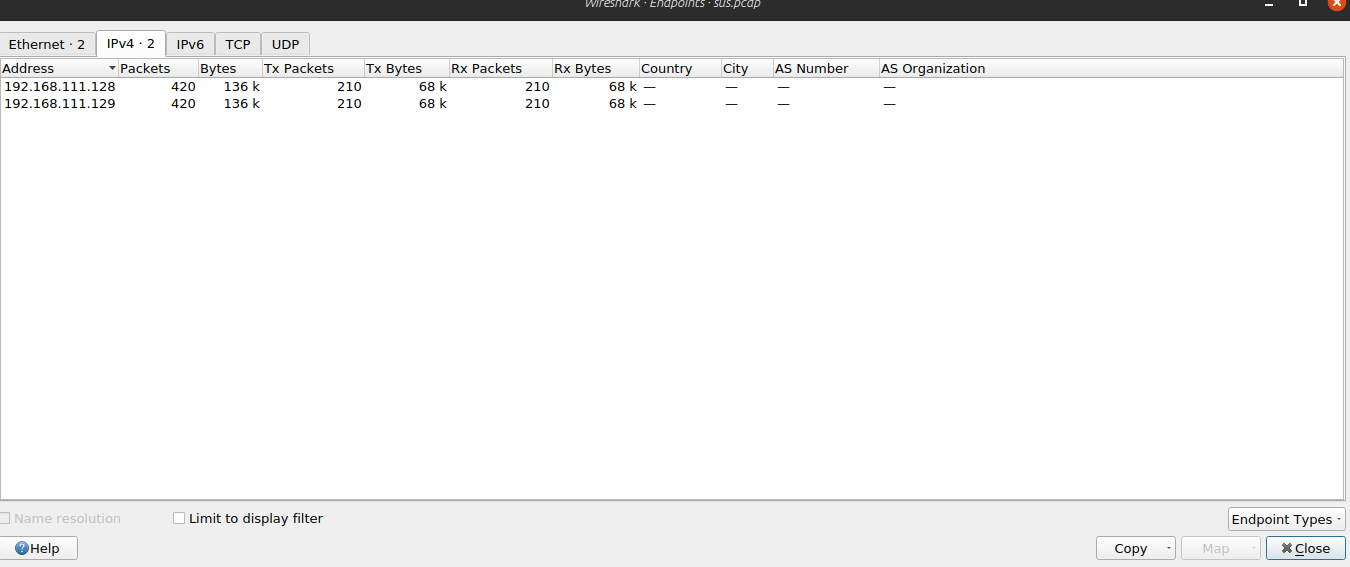
I also checked the number of endpoints also using the statistics/endpoints tab. and I had only 2 endpoints involved in all the captured packets.
With that summary information, my first assignment was to understand more about ICMP protocol
What is ICMP protocol
ICMP stands for Internet Control Message Protocol. It’s a protocol within the Internet Protocol Suite, used primarily for diagnostic and error messages in IP networks. ICMP messages are typically used by network devices, like routers and switches, to communicate with each other and with hosts.
Here are two simple examples of how ICMP is used:
Ping:One of the most common uses of ICMP is the “ping” command. When you ping a device, your computer sends an ICMP Echo Request message to that device’s IP address. If the device is reachable and operational, it will respond with an ICMP Echo Reply message. This helps in determining whether a host is reachable and how long it takes for packets to travel to and from that host. For example, you might use the ping command to check if a website is up and how quickly it responds
Traceroute:Traceroute is another tool that uses ICMP. When you run a traceroute command, your computer sends a series of ICMP Echo Request messages with varying Time-to-Live (TTL) values. Each router along the path to the destination decrements the TTL value, and if it reaches zero, the router discards the packet and sends back an ICMP Time Exceeded message to the source. By analyzing the ICMP Time Exceeded messages received from each router, traceroute can map the path packets take from your computer to the destination, helping to diagnose network routing issues.
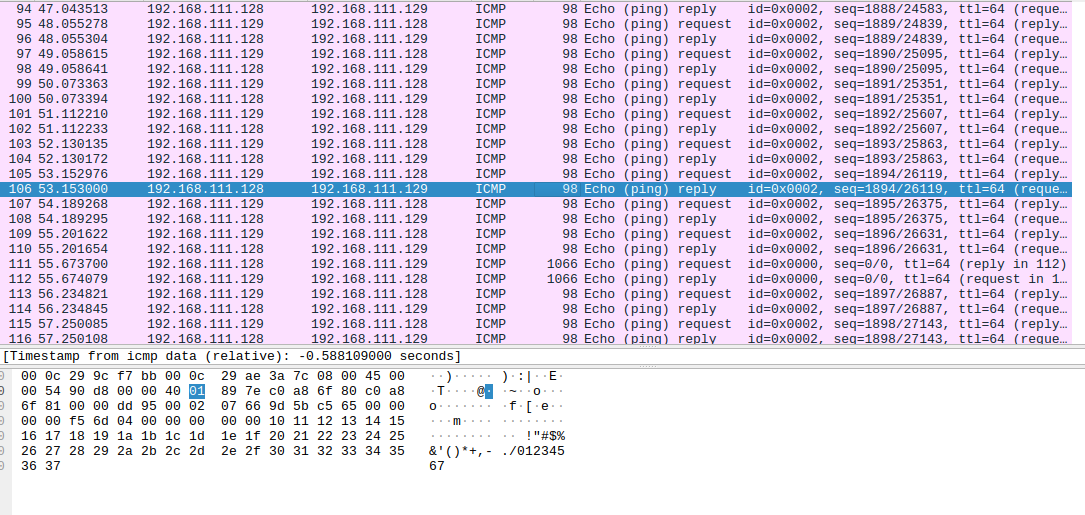
Looking athe packets, I found three main packets size , one was of 98 packets which was reply packets
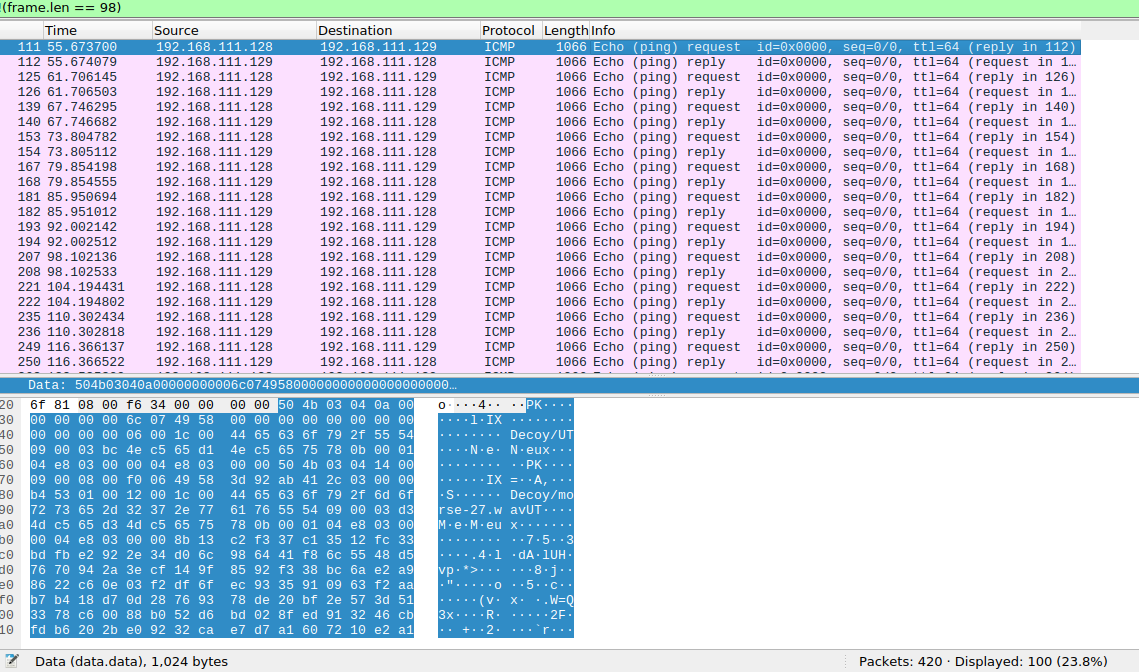
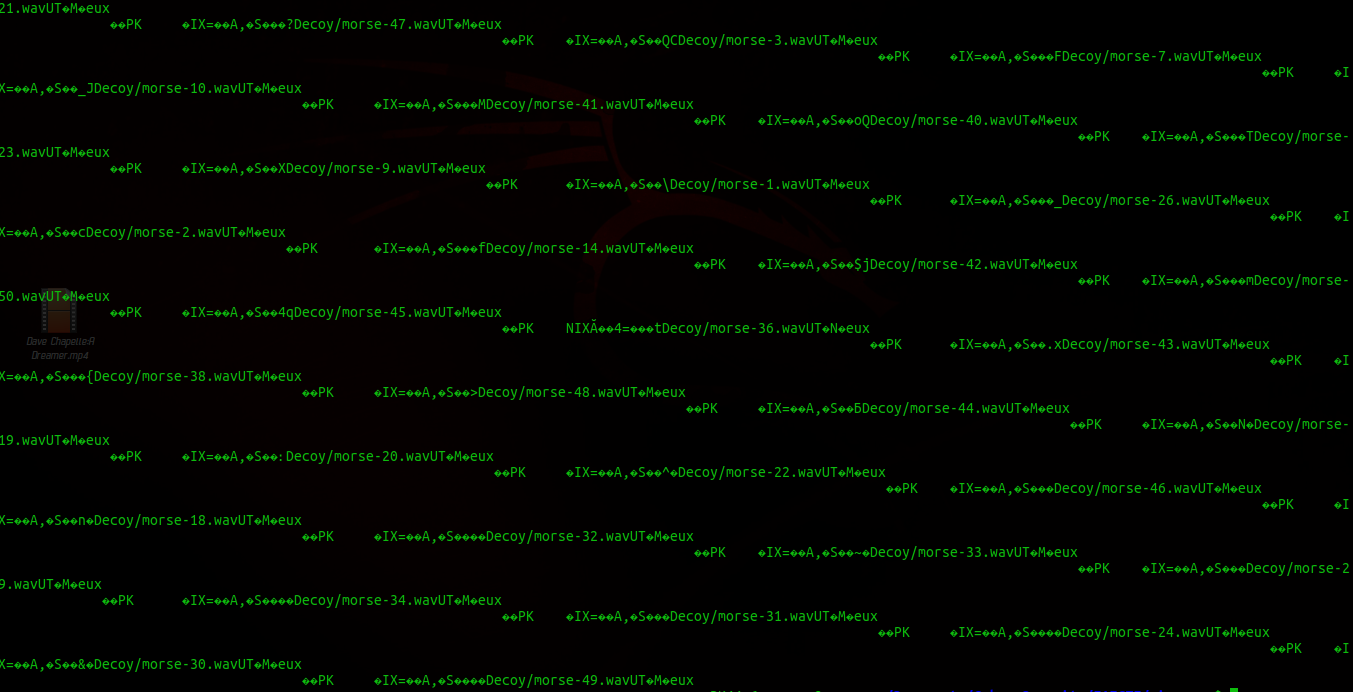
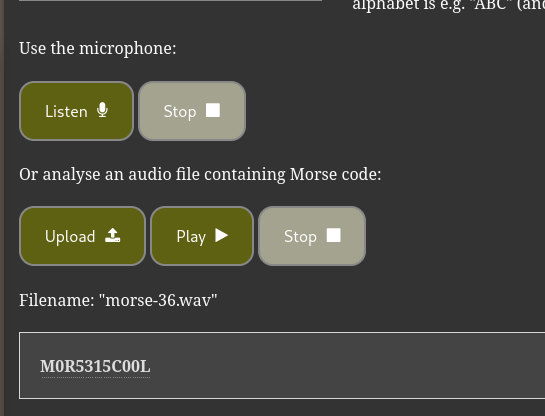
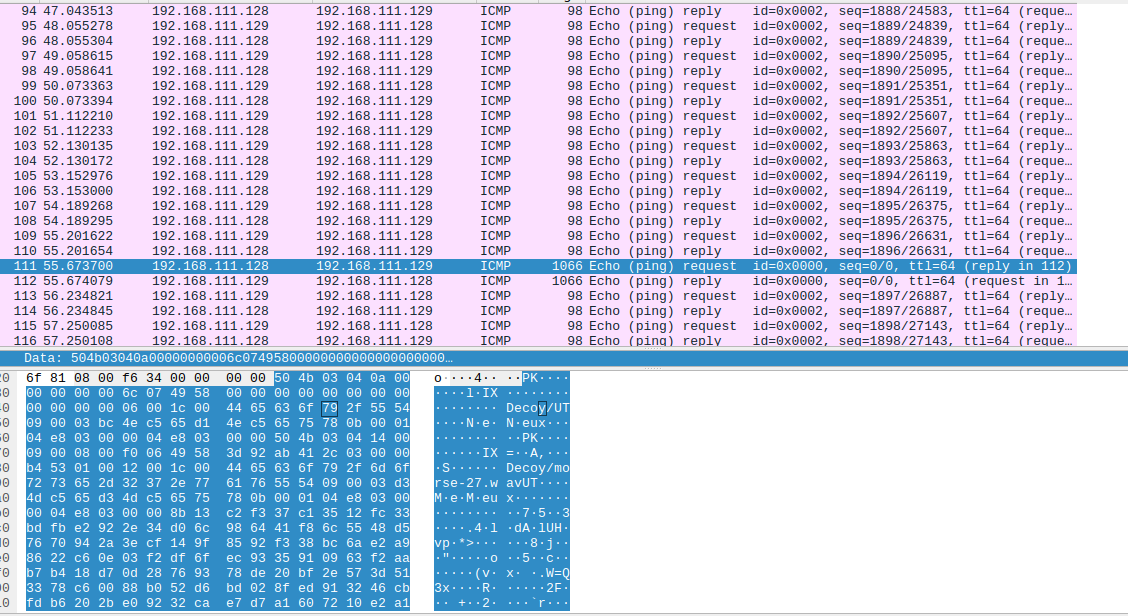
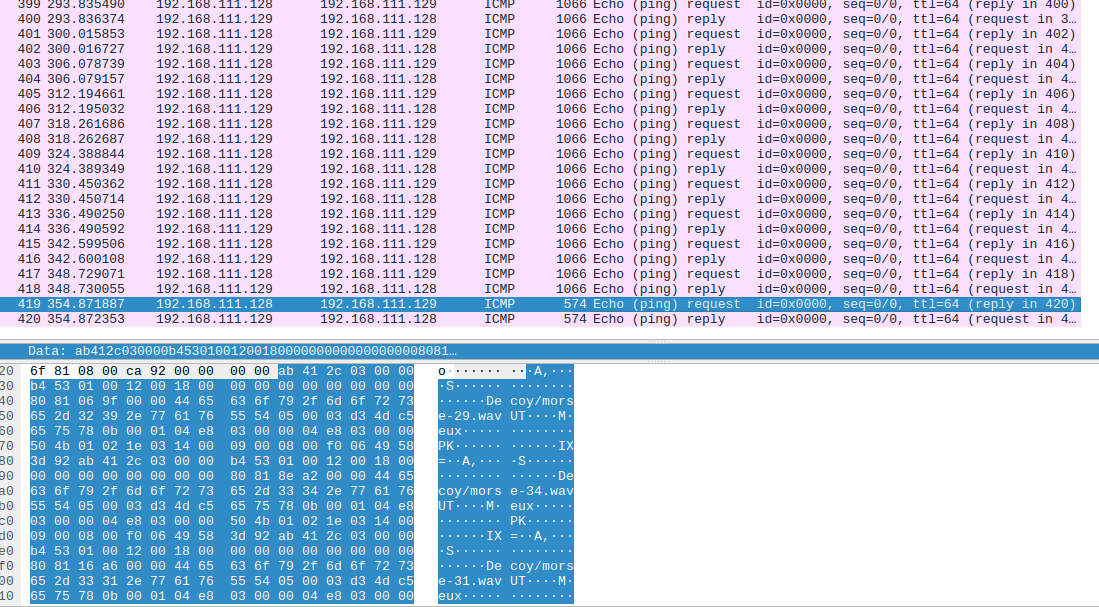
And request packects for request whose size wa 1066 and ahad some interesting strings
There was about 2 packets a request and reply of 574 size
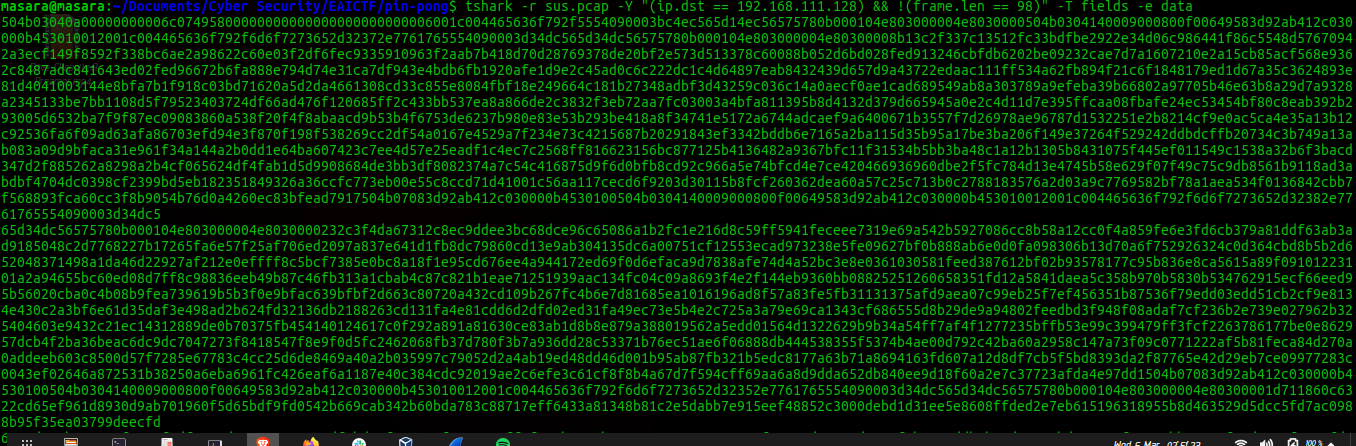
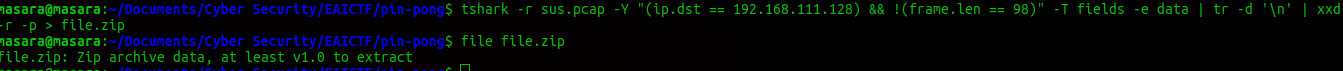
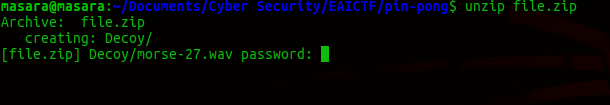
I resolved to start with the 1066 request packets which had interesting strings text .